Atomic Red Team
Description
Atomic Red Team allows every security team to test their controls by executing simple “atomic tests” that exercise the same techniques used by adversaries (all mapped to Mitre’s ATT&CK).
Purpose
The purpose of Atomic Red Team in DetectionLab is to allow the user to simulate TTPs and observe the resulting telemetry or create new detections.
Configuration Details
- Installed from
install-redteam.ps1 - The
Invoke-AtomicRedTeamexecution framework
Sample Usage
Import Powershell module and atomics-path:
Import-Module "C:\Tools\AtomicRedTeam\invoke-atomicredteam\Invoke-AtomicRedTeam.psd1" -Force
$PSDefaultParameterValues = @{"Invoke-AtomicTest:PathToAtomicsFolder"="C:\Tools\AtomicRedTeam\atomics"}
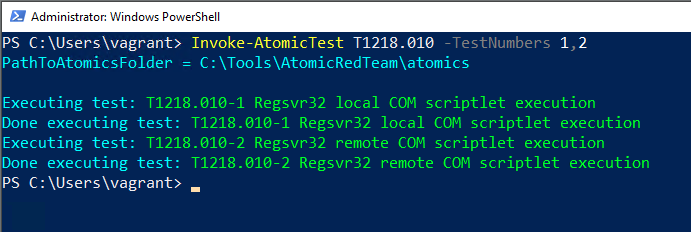
Run E.g. technique T1218.010 (Signed Binary Proxy Execution: Regsvr32):
Invoke-AtomicTest T1218.010 -TestNumbers 1,2
Run all techniques:
Invoke-AtomicTest All
More here: https://github.com/redcanaryco/invoke-atomicredteam/wiki/Execute-Atomic-Tests-(Local)
Data Location
This tools and test are located in C:\Tools\AtomicRedTeam\
This tool/application does not generate logs